Affordable Tech Deal in Auckland Wide, Cheap CCTV Install – OI -How to Automatically Create Build Backups in Visual Studio HRFSTech Computer Repair Website Design Cheap Service with Free Callouts
How to Automatically Create Build Backups in Visual Studio
If you are a one man development team, you probably don’t really have the need for a full blown version control system, yet creating source code backups for each released version is undoubtedly important.
By leveraging the power of post-build events and a simple batch script, you can easily add the ability to have Visual Studio automatically create a source code backup for each release code build.
How it works
Our solution is simple: whenever a successful build event occurs, we have a batch script run which creates a compressed archive (optionally tagged and timestamped) of all files in the respective Visual Studio project folder.
That’s it. All you have to do is follow the steps below.
Setting up automatic build backups
First you will need to download and extract the batch script file from the link at the bottom of the article. Additionally, you will need the 7-Zip command line tool (this is included with a the ‘full’ version of the Project Build Backup script, or you can download it separately). In our example, we extracted these files to the directory “C:\Tools”, but any location will work.
Open your Visual Studio Project properties, by double-clicking on My Project under the respective project.
In the project properties, go to the Compile section.
In the bottom right corner, click the Build Events button.
In our case, we want to make a backup after a successful compile action. Make sure you have the option to run the post-build event “On successful build” and then click the Edit Post-build button.
The command below creates a build backup only for the compile of the Release configuration (this is what IF condition checks for) as, realistically, we probably don’t want to make a backup of each Debug/testing build. Additionally, the current timestamp will be appended (/D switch) with the backup file being in 7z file format (/7z) as opposed to zip. By adding the /T “$(ConfigurationName)” as a parameter, we are appending the build type (Release in this case) to the name of the backup file.
IF “$(ConfigurationName)” == “Release” CALL C:\Tools\ProjectBuildBackup.bat “$(SolutionDir)” “$(ProjectDir)” “$(ProjectName)” /T “$(ConfigurationName)” /D /7z
Using the Macros button, you can have Visual Studio prefill project specific information so no hardcoding is required. You can adjust this command as needed (especially the location of the batch file), but the first three parameters will likely not need to be changed.
It is important to keep in mind that post-event operations run regardless of the project configuration selected. This is why we need to add the IF “$(ConfigurationName)” == “Release” statement – otherwise the backup action would occur on every successful build event.
Once you finish your command and apply it, the command string should appear in the Post-build events section.
Note that while the “CALL” command is not technically required, it is highly recommended, as if this is omitted then any events added after this may not execute.
Now whenever you run a compile/build with your project in the Release configuration, you will see the output from the build backup operation.
Each successful Release build creates a new timestamped archive with the solution folder in a subdirectory, “Builds” (which can be custom defined with the /O switch if needed).
The contents of each backup is the full Visual Studio project – source files, configuration settings, compiled binaries, and all – which makes this a true point in time backup.

Not a replacement for a full version control system
In closing, we just want to reiterate that this tool is not intended to replace a full blown version control system. It is simply a useful tool for developers to create snapshots of their project’s source code after each compilation.
In the event you ever have to go back and examine a prior version, having a ready-to-use (just extract to a new directory) project file for a point in time compilation can really come in handy.
Links
Download Project Build Backup Script
Download 7-Zip Command Line Tool (Note – the 7za utility is also bundled with a download from the Project Build Backup script)
16 total views, no views today
- March 31, 2015
–
All 2014 Knowledge System
Search for an Operating Instructions if you can’t find it here.
How to Kill a Desktop Application or Background Process on Linux
Windows has Ctrl+Alt+Delete and Macs have Command+Option+Escape to force frozen applications to close. Linux has its own ways of “killing” those misbehaving processes, whether they’re graphical windows or background processes.
The exact graphical tools you can use will depend on your desktop environment, as eachdesktop environment brings different tools to the table. But most of them are pretty similar.
From a Graphical Desktop

Modern Linux desktops deal with this fairly well, and it can be surprisingly automatic. If an application isn’t responding, a desktop with a compositiong manager will often gray the entire window out to show it isn’t responding.
Read More
How to Test Your Internet Speed from the Command Line

How to Enable Automatic Security Updates on Ubuntu Server
There’s nothing more tedious as a system administrator than running security updates on a dozen servers every single day. Luckily Ubuntu will let you automate stable security updates so you’re never at risk.
All you need to do is run this one single command on your server:
sudo dpkg-reconfigure -plow unattended-upgrades
If you are logged in as root you can skip the sudo, of course.

Read More
Office file types fail to Open From Server
When you try to open or download a Microsoft Office file that is stored on a web server or a third-party web server, the associated Office application starts, but the selected file is not opened or downloaded. For example, the Office file is stored on a SharePoint server or a Web Distributed Authoring and Versioning (WebDAV) server. You get following error message:
When this problem occurs, try using HTTPS instead of HTTP to access the Office files. For example, use https://www.site.cominstead of http://www.site.com. If you still can’t open the Office files, contact the site server administrator.
Cause
This problem occurs when the following conditions are true:
- The server is configured for Basic authentication.
Read More
Some Useful Day-To-Day Software
Microsoft Office 2010, 2013: Download Link – Call us for “activation” – Direct Link
YouTube Downloader: YTD Video Downloader – Important: For installation, follow this steps Otherwise your computer might get effected by virus.
VLC Player: Download link – Direct Link
Click Here For More
Installing windows flash cards (Q&A) 
The price for Windows 7 is the same regardless of the edition and type of license you purchaseAnswer: False
The OEM version of Windows 7 can only be installed on a new PC for resale.
Answer: True
When a partition is formatted with a file system and assigned a drive letter it is called a volume.Answer: True
Read More
Office 365 Unified Messaging with Lync 2013 On Premise
Lync 2013 Enterprise Voice On Premise – Exchange 2010 Sp3 Hybrid with The New Office 365 tenant (Wave 15)
First of all open up a PS shell on your Lync FE on premise then run:
- Set-csaccessedgeconfiguration –allowfederatedusers $true
- New-CsHostingProvider -Identity “Exchange Online” -Enabled $True -EnabledSharedAddressSpace $True -HostsOCSUsers $False -ProxyFqdn “exap.um.outlook.com” -IsLocal $False -VerificationLevel UseSourceVerification
Read More
How to “built” Active Directory in Windows Server 2012
AD DS domain controllers also host the service that authenticates user and computer accountswhen they log on to the domain. Because AD DS stores information about all of the objects in the domain, and all users and computers must connect to AD DS domain controllers when signing into the network, AD DS is the primary means by which you can configure and manage user and computer accounts on your network.
So today, I will guide you on how to “built” @ deploy.. and my students always name this process as a “Installation of Active Directory in Windows Server 2012“.
For this Simple Guide, I’m using Core I5-3470 3.20Ghz proc & 3.8GB RAM, all the process using Hyper-V & private network.
Let’s get started..
1 – Double confirm the Windows Server 2012 that you are using still in Workgroup configuration.
Read More
How to Rename Domain Name in Windows Server 2012 (Cluster Hyper-V and/or in-house exchange-DC?
For this exercises, I’m using MCT courseware from 20410B (Installing and Configuring Windows Server 2012).
The existing domain is ADATUM.COM and I will rename it to CPX.LOCAL.
** for those who want to built your own AD and try this exercises, please refer to my previous post
So, let get started…
1 – Open your System Properties and check your existing domain name, if you see from my Windows Server 2012 system properties, my existing domain name isAdatum.com. This will be change to cpx.local in the short while.
Read More
Installing .NET Framework 3.5 in Windows 8 and in Windows Server 2012
Windows 8 or use this for Windows Server 2012 R2 if virtually under a Windows 8 or 8.1 Pro etc.
In Windows 8 open the Programs and Features dialog. For me the easiest way to access this dialog is via the Windows+X admin menu:
Or if windows is added to the domain or no internet access then run installation thru command line:
dism /online /enable-feature /featurename:NetFx3 /All /Source:D:\sources\sxs /LimitAccess
Read More
How to Install Windows 8.1 without a Product Key
- Step 1: Once you’ve created a Bootable windows 8.1 USB Flash drive. Create a Text document and copy the following text in it.
[EditionID]
Core
[Channel]
Retail
[VL]
0
Read More
How to Build a Bootable USB Drive? or How to Install an Operating System from a USB Device?
1. Get a USB Drive of sufficient size to contain the OS installation files you desire to install. (If you were going to install Windows 7 this drive woul dneed to be at least 4 GB in size)
Short Version:
- Insert a USB flash drive into a running computer.
- Open a Command Prompt window as an administrator.
- Type diskpart.
- In the new command line window that opens, to determine the USB flash drive number or drive letter, at the command prompt, type list disk, and then click ENTER. The list disk command displays all the disks on the computer. Note the drive number or drive letter of the USB flash drive.
Read More
Fine Tune Star Receiver
STAR Rx can accept wide range of input signal power i.e. –20 to –60 dBm. However, the STAR Rx must be configured its “stargain” according to the signal power. Stargain controls the amplifier for the input signal. The STAR input signal can be high or low depending on the configuration of the BDC, dividers and other things.
Instructions on how to setup your email account for Microsoft Outlook.
Click on below links to Download Instructions.
How to adjust the DVB power levels in ViaSat System
ViaSat power level change was done at 8:18 PM by 1 dB and then at 8:32 PM by another 1 dB and changed back at 8:45 PM. I couldn’t see much differences once 1 dB changes was done, but at 2 dB ViaSat changes ACM gain increased 35%. For more details
How to Change Time Zone in iDirect due to Daylight Saving
Setting the Date and Time on the NMS Servers TZ select – For More details
17 total views, no views today
- March 31, 2015
–
How to Enable Pin Sign-in For Domain Users on Windows 8
How to Enable Pin Sign-in For Domain Users on Windows 8
Domain users are not allowed to sign in with a Pin by default. However, using a little bit of GPO, we can change that.
How to Enable Pin Sign On For Domain Users on Windows 8
Press the Win + R keyboard combination to open a run box then type “gpedit.msc” and press enter.
When the Group Policy editor opens, navigate to:
Computer Configuration\Administrative Templates\System\Logon
On the right hand side, double click on the “Turn on PIN sign-in” setting.
Now switch the radio button from Not Configured to Enabled, then click Apply.
Once the setting has been activated, you need to refresh your current Group Policy settings. To do that, open a run box using the Win + R keyboard combo and type the following, then press enter.
gpupdate /force
Of course, this will only be useful in a domain environment, in which case you could assign this group policy setting to an OU in Active Directory. That’s all there is to it.
26 total views, no views today
- March 23, 2015
–
How to Kill a Desktop Application or Background Process on Linux
How to Kill a Desktop Application or Background Process on Linux

Windows has Ctrl+Alt+Delete and Macs have Command+Option+Escape to force frozen applications to close. Linux has its own ways of “killing” those misbehaving processes, whether they’re graphical windows or background processes.
The exact graphical tools you can use will depend on your desktop environment, as each desktop environment brings different tools to the table. But most of them are pretty similar.
From a Graphical Desktop
Modern Linux desktops deal with this fairly well, and it can be surprisingly automatic. If an application isn’t responding, a desktop with a composition manager will often gray the entire window out to show it isn’t responding.
Click the X button on the window’s titlebar and the window manager will often inform you that the window isn’t responding. You can either give it some time to respond or click an option like “Force Quit” to foricbly close the application.
On Linux, the window manager that paints the title bars is separate from the application itself, so it usually responds even if the window won’t. Some windows do paint their own interfaces, though, so this may not always work.

The “xkill” application can help you quickly kill any graphical window on your desktop.
Depending on your desktop environment and its configuration, you may be able to activate this shortcut by pressing Ctrl+Alt+Esc. You could also just run the xkill command — you could open a Terminal window, type xkill without the quotes, and press Enter. Or, you could press a shortcut like Alt+F2, which opens the “Run Command” dialog on Ubuntu’s Unity desktop and many others. Type xkill into the dialog and press Enter.
Your cursor will change to an X. Click a window and the xkill utility will determine what process is associated with that window, and then immediately kill that process. The window will instantly vanish and close.

Your Linux desktop probably has a tool that works similarly to the Task Manager on Windows, too. On Ubuntu’s Unity desktop, GNOME, and other GNOME-based desktops, this is the System Monitor utility. Open the System Monitor utility to see a list of running proesses — including background ones. You can also forcibly kill processes from here if they’re misbehaving.

From the Terminal
Let’s say Firefox is running in the background and we want to kill it from the terminal. The standard kill command takes a process ID number, so you’ll need to find it first.
For example, you could run a command like:
ps aux | grep firefox
Which would list all processes and pipe that list to the grep command, which will filter it and print only lines containing Firefox. (The second line you’ll see is the grep process itself.) You can also get the process ID from the top command and many other places.
Take the process ID number from the Firefox process — just to the right of the username — and provide it to the kill command. That is, run the command like so:
kill ####
If the process is running as another user, you’ll need to become the root user first — or at least run the kill command with the sudo command, like so:
sudo kill ####

That’s a basic method, but it isn’t quite the fastest. The pgrep and pkill commands help streamline this. For example, run “pgrep firefox” to see the process ID of the running Firefox process. You could then feed that number to the kill command.
Or, skip all that and run “pkill firefox” to kill the Firefox process without knowing its number. pkill performs some basic pattern-matching — it’ll try to find processes with names containing firefox.

The killall command is like pkill, but a bit more precise. It’ll kill all running processes with a specific name. So running “killall firefox” will kill all running processes named “firefox,” but not any processes that just have firefox in their names.

These are far from the only commands included on Linux for managing processes. If you’re using some type of server administration software, it may also have helpful ways to kill and restart processes.
System services work different from processes — you’ll need to use specific commands to bring down, restart, or bring up services. Those specific commands can be different on different Linux distributions.
25 total views, no views today
- March 23, 2015
–
How to Enable Automatic Security Updates on Ubuntu Server
How to Enable Automatic Security Updates on Ubuntu Server

There’s nothing more tedious as a system administrator than running security updates on a dozen servers every single day. Luckily Ubuntu will let you automate stable security updates so you’re never at risk.
All you need to do is run this one single command on your server:
sudo dpkg-reconfigure -plow unattended-upgrades
If you are logged in as root you can skip the sudo, of course.

Once you run the command you’ll be presented with a very pink screen that might prompt you to say Ok.

If your terminal was a little wider you probably would see it all on a single page, but either way you’ll be asked if you want to automatically download and install stable updates. Select Yes.

The utility will write out the necessary configuration files, and security updates should become automated. Note that by default it’s going to wait to check once a day, so it’s not like any pending security updates will be instantly installed once you change this setting, but you shouldn’t have to install security updates ever again.
32 total views, 1 views today
- March 19, 2015
–
Office file types fail to Open From Server
Office file types fail to Open From Server
When you try to open or download a Microsoft Office file that is stored on a web server or a third-party web server, the associated Office application starts, but the selected file is not opened or downloaded. For example, the Office file is stored on a SharePoint server or a Web Distributed Authoring and Versioning (WebDAV) server. You get following error message:
When this problem occurs, try using HTTPS instead of HTTP to access the Office files. For example, use https://www.site.cominstead of http://www.site.com. If you still can’t open the Office files, contact the site server administrator.
Cause
This problem occurs when the following conditions are true:
- The server is configured for Basic authentication.
- The connection between your computer and the web server does not use Secure Sockets Layer (SSL).
By default, file operations that use Basic authentication over a non-SSL HTTP connection are disabled in Office 2010 and Office 2013 applications.
When Basic authentication is disabled, one of the following events occurs:
- The client application uses a different authentication method. This occurs if the server supports a different authentication method.
- The request fails (for details about what happens when a request fails, see the list in the “Additional symptom details” section).
Resolution
Workaround
To work around this problem, let Office 2013 and Office 2010 applications connect to a web server by using Basic authentication over a non-SSL connection.Warning When you enable Basic authentication without SSL, you are subject to a significant security risk.
About Basic authentication and its security risk
Basic authentication requires users to a valid user name and password to access content. This authentication method does not require a specific browser, and all major browsers support it. Basic authentication also works across firewalls and proxy servers. For these reasons, it is a good choice when you want to restrict access to some, but not all, content on a server.However, the disadvantage of Basic authentication is that it transmits unencrypted base64-encoded passwords over the network. If the password is intercepted over the network by a network sniffer, an unauthorized user can determine the user name and password, and can then reuse these credentials. It is because of this security risk that Office 2010 applications disable Basic authentication over a non-SSL connection in the default configuration.You should use Basic authentication only when you know that the connection between the client and the server is secure. The connection should be established either over a dedicated line or by using SSL encryption and Transport Layer Security (TLS). For example, to use Basic authentication with WebDAV, you should configure SSL encryption.
For more information about Basic authentication, see Basic authentication and Configure Basic authentication (IIS 7).
For more information about SSL and certificates, see SSL and certificates.
Enable Basic authentication over a non-SSL connection
Note For Office 2013 and Office 2010 applications, both steps are required. For other Office applications, only step 1 is required.
Step 1: Configure WebDAV Redirector on the client
Note This step is required for applications in the 2007 Office suite and in Office 2013 and Office 2010.
On the client computer, configure the WebDAV Redirector to enable Basic authentication over non-SSL connections.
Important Follow the steps in this section carefully. Serious problems might occur if you modify the registry incorrectly. Before you modify it, back up the registry for restoration in case problems occur.
Windows XP and Windows Server 2003
To enable Basic authentication on the client computer, follow these steps:
- Click Start, click Run, type regedit, and then click OK.
- Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WebClient\Parameters
- On the Edit menu, point to New, and then click DWORD Value.
- Type UseBasicAuth, and then press Enter.
- Right-click UseBasicAuth, and then click Modify.
- In the Value data box, type 1, and then click OK.Note Basic authentication is enabled if the UseBasicAuth registry entry is set to a nonzero value. Basic authentication is disabled if the UseBasicAuth registry entry is not present, or if the UseBasicAuth registry entry is set to 0 (zero).The mapping is as follows:
0 – Basic authentication disabled
1 – Basic authentication enabled for SSL connections only
2 – Basic authentication enabled for SSL and non-SSL connections - Exit Registry Editor, and then restart the computer.
Windows Vista, Windows 7, and Windows 8 (Inc 8.1 & Pro)
To enable Basic authentication on the client computer, follow these steps:
- In Windows Vista or Windows 7, click Start, type regedit in the Start Search box, and then press Enter.In Windows 8, hold the Windows key (WINKEY) + F, highlight Apps in theMenu bar, type regedit in the Search box, and then press Enter.
- Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WebClient\Parameters
- On the Edit menu, point to New, and then click DWORD Value.
- Type BasicAuthLevel, and then press Enter.
- Right-click BasicAuthLevel, and then click Modify.
- In the Value data box, type 2, and then click OK.Note The mapping is as follows:
0 – Basic authentication disabled
1 – Basic authentication enabled for SSL connections only
2 – Basic authentication enabled for SSL and non-SSL connections - Exit Registry Editor, and then restart the computer.
For more information about how to configure the WebDAV redirector to enable Basic authentication, click the following article number to view the article in the Microsoft Knowledge Base:
Step 2: Update the Registry on the client
Note This step is required for Office 2013 and Office 2010 applications.
On the client computer, add the BasicAuthLevel registry key and an appropriate value. To do this, follow these steps.
Important Follow the steps in this section carefully. Serious problems might occur if you modify the registry incorrectly. Before you modify it, back up the registry for restoration in case problems occur.
- Start Registry Editor.
- In Windows 8, hold the Windows key (WINKEY) + F, highlight Apps in the Menu bar, type regedit in the Searchbox, and then press Enter. If you are prompted for an administrator password or for confirmation, type the password, or provide confirmation.
- In Windows 7 or in Windows Vista, click Start, type regedit in the Start Search box, then press Enter. If you are prompted for an administrator password or for confirmation, type the password, or provide confirmation.
- In Windows XP, click Start, click Run, type regedit, and then click OK.
- Locate and then click one of the following registry subkeys:For Office 2010
HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\Internet
For Office 2013
HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Internet - On the Edit menu, point to New, and then click DWORD Value.
- Type BasicAuthLevel, and then press Enter.
- Right-click BasicAuthLevel, and then click Modify.
- In the Value data box, type 2, and then click OK.Note The mapping is as follows:
0 – Basic authentication disabled
1 – Basic authentication enabled for SSL connections only
2 – Basic authentication enabled for SSL and for non-SSL connections - Exit Registry Editor, and then restart the computer.
24 total views, no views today
- March 18, 2015
–
YouTube Downloader Installation Steps
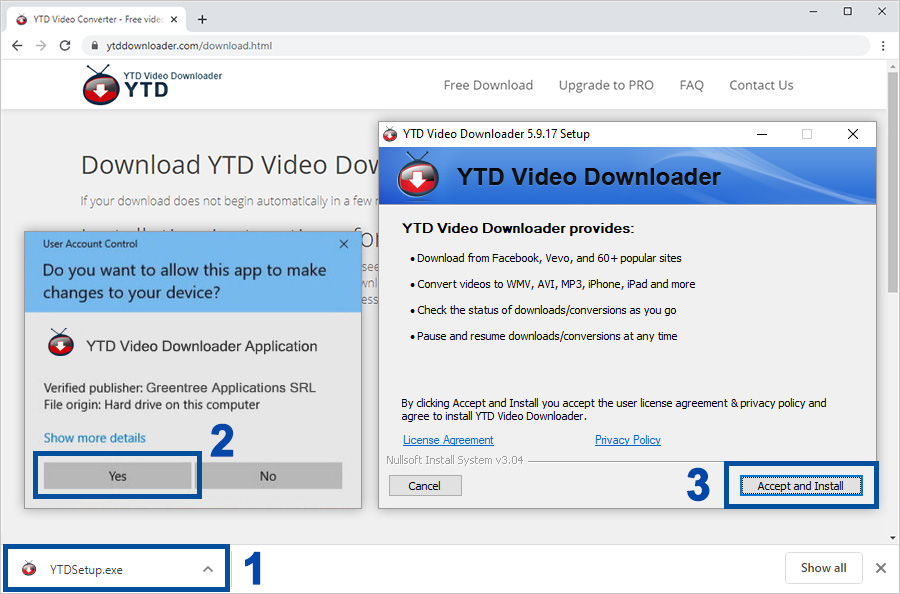
Important: Make sure you click cancel on below two steps
For any support, please fill in below forms with your details or call us.
36 total views, 1 views today
- March 18, 2015
–
Some Useful Day-To-Day Software
- YouTube Downloader: YTD Video Downloader – Important: For installation, follow this steps
- VLC Player: Download link
- Skype Day-To-Day Use: Download Here
- Microsoft Office 2010, 2013: Download Link – Call us for “activation”
- Torrent Download: Download Link – Give us a call BEFORE installing this. This comes with Spyware
22 total views, no views today
- March 18, 2015
–
Installing windows flash cards (Q&A)
Basic Q&A:
The price for Windows 7 is the same regardless of the edition and type of license you purchase
Answer: False
The OEM version of Windows 7 can only be installed on a new PC for resale.
Answer: True
When a partition is formatted with a file system and assigned a drive letter it is called a volume.
Answer: True
An upgrade from Windows Vista to Windows 7 carries applications and user settings forward into the new installation.
Answer: True
Which Windows 7 Edition is intended for business users and allows you to purchase multiple site licenses?
Answer: Windows 7 Professional
Which type of OS should you install for best performance when you have enough RAM?
Answer: 64 bit
What is it called when software is used to simulate the hardware of a physical computer?
Answer: Virtual Machine
A____boot allows you to install the new OS without disturbing the old one so you can boot to either OS.
Answer: Dual
What type of installation should you perform if you want to install a 64-bit version of Windows on a computer that already has a 32-bit OS installed?
Answer: Clean Install
What is the name of the directory database that controls access to a Windows Server domain?
Answer:Active Directory
Where should a user disable virus protection settings that might prevent the boot area of the hard drive from being altered? Answer: BIOS setup
Which network location option means that Network Discovery is turned off and you cannot join a homegroup or domain?
Answer: Public Network
For some brand-name computers, the hard drive contains a ______partition that can be used to reinstall Windows.
Answer: Hidden Recovery
The__________is used to change motherboard settings, finds a boot device, and contains instructions for running essential hardware before an OS is started.
Answer: BIOS
In a Windows_____,each computer maintains a list of users and their rights on that particular computer.
Answer: Workgroup
A Windows domain is a type of _____network, which is a network where resources are managed by a centralized computer. Answer: Client/server
Which of the following is used to uniquely identify a computer on a network?
Answer: IP Address
What important information is needed if you are installing an OEM version of Windows 7?
Answer: Product Key
After installation, how many days do you have to activate Windows 7?
Answer: 30
Contains instructions for running essential hardware devices before an operating system is started _________
Answer: System BIOS
A network that is managed by each computer without centralized control ____________.
Answer: Peer-to-peer network
A copy of an entire hard drive that includes Windows 7, drivers, and applications that are standard to all thA12:A45e computers that might use that copy.
Answer: Standard image
24 total views, no views today
- March 17, 2015
–
Office 365 Unified Messaging with Lync 2013 On Premise
Office 365 Unified Messaging with Lync 2013 On Premise
Lync 2013 Enterprise Voice On Premise – Exchange 2010 Sp3 Hybrid with The New Office 365 tenant (Wave 15)
First of all open up a PS shell on your Lync FE on premise then run:
- Set-csaccessedgeconfiguration –allowfederatedusers $true
- New-CsHostingProvider -Identity “Exchange Online” -Enabled $True -EnabledSharedAddressSpace $True -HostsOCSUsers $False -ProxyFqdn “exap.um.outlook.com” -IsLocal $False -VerificationLevel UseSourceVerification
- Get-csmanagementstorereplicationstatus ( to ensure replication has occured between all Lync servers make sure they all say true before moving on)
- Get-cshostingprovider -localstore to show the following

- Set-CsAccessEdgeConfiguration -UseDnsSrvRouting -AllowFederatedUsers 1 -EnablePartnerDiscovery 0
- New-CsHostedVoicemailPolicy -identity CloudUM -Destination exap.um.outlook.com -Description “Office 365 Voicemail” -Organization “tenantname.onmicrosoft.com” (Ensure you use the tenant name and NOT your on premise domain otherwise the traffic will not route and this will not work)
Log onto the O365 Wave 15 tenant
Go to Unified Messaging > UM Dial Plans > New

Then Edit the Dial Plan > Configure
For this you should try and match the company’s on premise configuration so that it matches but below is an example:






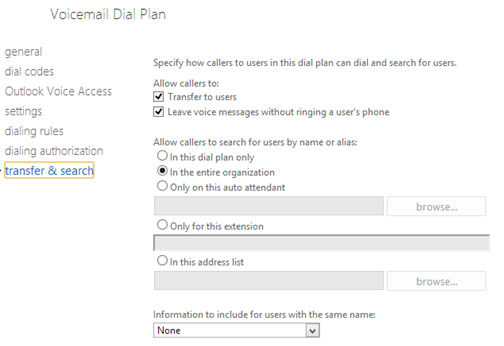
Then on premise Lync 2013 you need to create the Exchange UM Contact for O365 within Lync Powershell
- new-csexumcontact -displaynumber +44203XXXXX –sipaddress SIP:EX_UM_365_SA@yourdomain.com -registrarpool yourpool01.youcompany.com -ou “OU=User,DC=yourcompany,dc=com”
- Grant-cshostedvoicemailpolicy –identity “post the GUID that has been created” –policyname CloudUM
Then switch to Exchange Online Powershell
- Set-UMmailboxpolicy -identity “Policy Name in O365” -SourceForestPolicy “CloudUM”
- Set-UMmailboxpolicy -identity “Policy Name in O365” -SourceForestPolicy “On Premise UM Policy”
Then finally on your on premise Exchange 2010 SP3 server (Note this is only if Unified Messaging is already configured on premise so that when you migrate a UM mailbox it doesn’t fail otherwise if you don’t run this step the remote move request will fail)
- Set-UMmailboxpolicy -identity “On Premise UM Policy” -SourceForestPolicy “Policy Name in O365”
The Very last step is to configure the user. Now if you are setting up UM brand new then carry out the following steps but if you are migrating a user then only carry this out after the user has migrated to Office 365 or you have suspended the move before completion. As otherwise UM will route to the cloud and until the mailboxes exists the voicemail message will never be delivered to the end user as you cannot have a spilt UM in cloud and mailbox on premise and vice versa.
Within Lync 2013 PowerShell
- Grant-cshostedvoicemailpolicy –identity “accountname” –policyname CloudUM
- Run get cs-user –identity “accountname” and check that hostedvoicemail is set to true if not run the following command.
- Set-csuser –identity “youraccount” –hostedvoicemail $true
Finally force dirsync and then if the account in 365 doesn’t show unified messaging enable set then set it within the Exchange console in 365.
Keyword:
Affordable Cheap Computer Repair – Cheap CCTV Install – Cheap Website Design – Cheap CCTV Package – Cheap Laptop Repair – Cheap Virus Removal – Cheap GPS Installs in Auckland, Penrose, South Auckland, Penrose, Greenlane, Albany, Manurewa Otara, Panmure Mount Wellington Manukau CCTV installs in Auckland, Manukau CCTV install, Otahuhu, Ellerslie, Panmure, Penrose, Onehunga, North Shore, St Heliers, Mount Wellington, Manukau Computer Repairs Auckland Central – Parnell – New Market – Remuera – Epsom – Mission Bay – St Heliers















