As an IT Pro, I routinely monitor employees computers and emails only if require investigations. It’s essential in a work environment for administrative purposes as well as for security. Monitoring email, for example, allows you to block attachments that could contain a virus or spyware. The only time I have to connect to a users computer and do work directly on their computer is to fix a problem.
However, if you feel that you are being monitored when you shouldn’t be, there are a few little tricks you can use to determine if you’re right. First off, to monitor someones computer means that they can watch everything that you are doing on your computer in real time. Blocking porn sites, removing attachments or blocking spam before it gets to your inbox, etc is not really monitoring, but more like filtering.

The one BIG problem I want to emphasize before moving on is that if you are in a corporate environment and think you’re being monitored, you should assume they can see EVERYTHING you do on the computer. Also, assume that you won’t be able to actually find the software that is recording everything. In corporate environments, the computers are so customized and reconfigured that it’s nearly impossible to detect anything unless you’re a hacker. This article is more geared towards home users who thinks a friend or family member is trying to monitor them.
Computer Monitoring
So now, if you still think someone is spying on you, here’s what you can do! The easiest and simplest way someone can log into your computer is by using remote desktop. The good thing is that Windows does not support multiple concurrent connections while someone is logged into the console (there is a hack for this, but I would not worry about). What this means is that if you’re logged into your XP, 7 or Windows 8 computer and someone were to connect to it using the BUILT-IN REMOTE DESKTOP feature of Windows, your screen would become locked and it would tell tell you who is connected.
So why is that useful? It’s useful because it means that in order for someone to connect to YOUR session without you noticing or your screen being taken over, they have use third-party software. However, in 2014, no one is going to be that obvious and it’s a lot harder to detect third-party software stealth software.
If we’re looking for third-party software, which is usually referred to as remote control software or virtual network computing (VNC) software, we have to start from scratch. Usually, when someone installs this type of software on your computer, they have to do it while you’re not there and they have to restart your computer. So the first thing that could clue you off is if your computer has been restarted and you don’t remember doing it.
Secondly, you should check in your Start Menu – All Programs and to see whether or not something like VNC, RealVNC, TightVNC, UltraVNC, LogMeIn, GoToMyPC, etc is installed. A lot of times people are sloppy and figure that a normal user won’t know what a piece of software is and will simply ignore it. If any of those programs are installed, then someone can connect to your computer without you knowing it as long as the program is running in the background as a Windows service.
That brings us to the third point. Usually, if one of the above listed programs are installed, there will be an icon for it in the task bar because it needs to be constantly running to work.
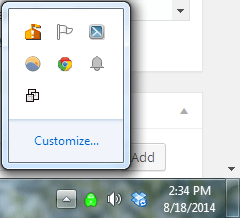
Check all of your icons (even the hidden ones) and see what is running. If you find something you’ve not heard of, do a quick Google search to see what pops up. It’s pretty easy for monitoring software to hide the taskbar icon, so if you don’t see anything unusual there, it doesn’t mean you don’t have monitoring software installed.
So if nothing is showing up in the obvious places, let’s move on to the more complicated stuff.
Check Firewall Ports
Again, because these are third-party apps, they have to connect to Windows on different communication ports. Ports are simply a virtual data connection by which computers share information directly. As you may already know, Windows comes with a built-in firewall that blocks many of the incoming ports for security reasons. If you’re not running an FTP site, why should your port 23 be open, right?
So in order for these third-party apps to connect to your computer, they must come through a port, which has to be open on your computer. You can check all the open ports by going to Start, Control Panel, andWindows Firewall. Then click on Allow a program of feature through Windows Firewall on the left hand side.
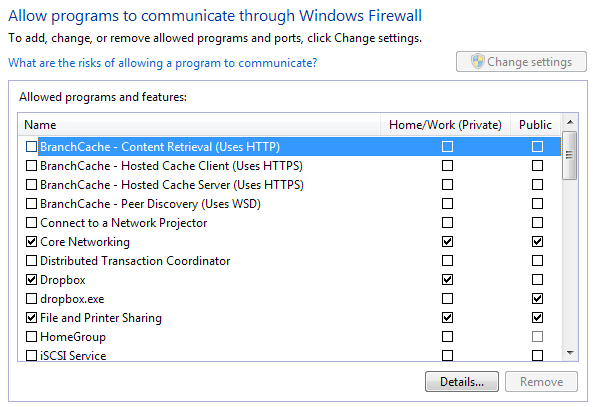
Here you’ll see see a list of programs with check boxes next to them. The ones that are checked are “open” and the unchecked or unlisted ones are “closed”. Go through the list and see if there is a program you’re not familiar with or that matches VNC, remote control, etc. If so, you can block the program by un-checking the box for it!
Check Outbound Connections
Unfortunately, it’s a bit more complicated than this. In some instances, there may be an incoming connection, but in many cases, the software installed on your computer will only have an outbound connection to a server. In Windows, all outbounds connections are allowed, which means nothing is blocked. If all the spying software does is record data and send it to a server, then it only uses an outbound connection and therefore won’t show up in that firewall list.
In order to catch a program like that, we have to see outbound connections from our computer to servers. There are a whole host of ways we can do this and I’m going to talk about one or two here. Like I said earlier, it gets a bit complicated now because we’re dealing with really stealthy software and you’re not going to find it easily.
Firstly, download a program called TCPView from Microsoft or ANZ Tech Website. It’s a very small file and you don’t even have to install it, just unzip it and double-click on Tcpview. The main window will look like this and probably make no sense.
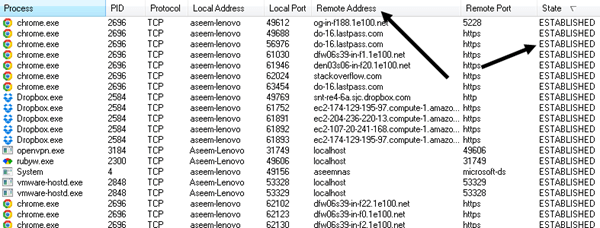
Basically, it’s showing you all the connections from your computer to other computers. On the left side is the process name, which will be the programs running, i.e. Chrome, Dropbox, etc. The only other columns we need to look at are Remote Address and State. Go ahead and sort by State column and look at all of them processes listed under ESTABLISHED. Established means there is currently an open connection. Note that the spying software may not always be connected to the remote server, so it’s a good idea to leave this program open and monitor for any new processes that may show up under the established state.
What you want to do is filter out that list to processes whose name you don’t recognize. Chrome and Dropbox are fine and no cause for alarm, but what’s openvpn.exe and rubyw.exe? Well, in my case, I use a VPN to connect to the Internet so those process are for my VPN service. However, you can just Google those services and quickly figure that out yourself. VPN software is not spying software, so no worries there. When you search for a process, you’ll instantly be able to tell whether or not it’s safe by just looking at the search results.
Another thing you want to check are the far right columns called Sent Packets, Sent Bytes, etc. Sort by Sent Bytes and you can instantly see which process is sending the most data from your computer. If someone is monitoring your computer, they have to be sending the data somwhere, so unless the process is hidden extremely well, you should see it here.
Process Explorer
Another program you can use to find all the processes running on your computer is Process Explorer from Microsoft. When you run it, you’ll see a whole lot of information about every single process and even child processes running inside parent processes.
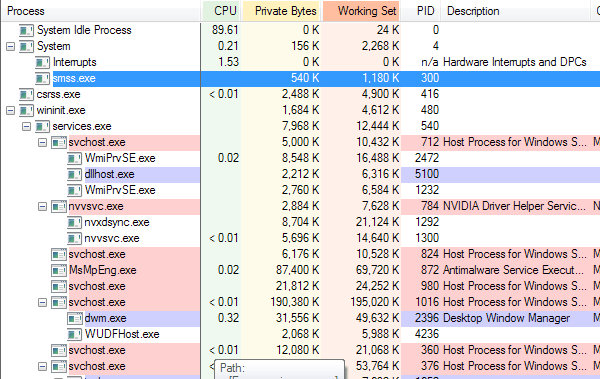
Process Explorer is pretty awesome because it connects up with VirusTotal and can tell you instantly if a process has been detected as malware or not. To do that, click on Options, VirusTotal.com and then click on Check VirusTotal.com. It’ll bring you to their website to read the TOS, just close that out and click Yeson the dialog in the program.
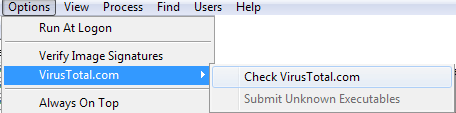
Once you do that, you’ll see a new column that shows the last scan detection rate for a lot of the processes. It won’t be able to get the value for all processes, but it’s better than nothing. For the ones that don’t have a score, go ahead and manually search for those processes in Google. For the ones with scores, you want it to pretty much say 0/XX. If it’s not 0, go ahead and Google the process or click on the numbers to be taken to the VirusTotal website for that process.
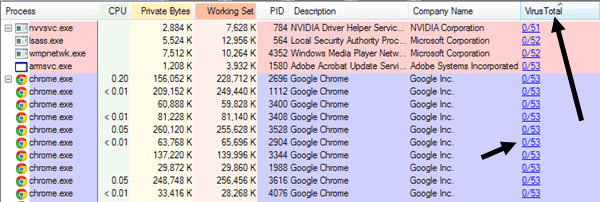
I also tend to sort the list by Company Name and any process that doesn’t have a company listed, I Google to check. However, even with these programs you still may not see all the processes.
Rootkits
There are also a class stealth programs called rootkits, which the two programs above won’t even be able to see. In this case, if you found nothing suspicious when checking all the processes above, you’ll need to try even more robust tools. Another good tool from Microsoft is Rootkit Revealer, however it’s very old.
Other good anti-rootkit tools are Malwarebytes Anti-Rootkit Beta, which I would highly recommend since their anti-malware tool was ranked #1 in 2014. Another popular one is GMER.
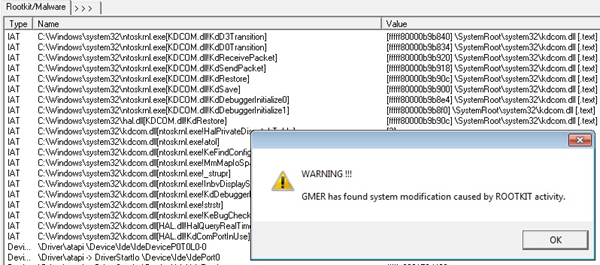
I suggest you install these tools and run them. If they find anything, remove or delete whatever they suggest. In addition, you should instal anti-malware and anti-virus software. A lot of these stealth programs that people use are considered malware/viruses, so they will get removed if you run the appropriate software. If something gets detected, make sure to Google it so you can find out whether it was monitoring software or not.
Email & Web Site Monitoring
To check whether your email is being monitored is also complicated, but we’ll stick with the easy stuff for this article. Whenever you send an email from Outlook or some email client on your computer, it always has to connect to an email server. Now it can either connect directly or it can connect through what is called a proxy server, which takes a request, alters or checks it, and forwards it on to another server.
If you’re going through a proxy server for email or web browsing, than the web sites you access or the emails you write can be saved and viewed later on. You can check for both and here’s how. For IE, go toTools, then Internet Options. Click on the Connections tab and choose LAN Settings.
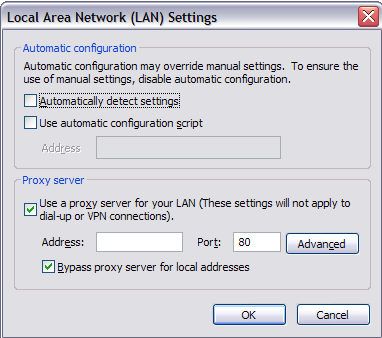
If the Proxy Server box is checked and it has a local IP address with a port number, then that means you’re going through a local server first before it reaches the web server. This means that any web site you visit first goes through another server running some kind of software that either blocks the address or simply logs it. The only time you would be somewhat safe is if the site you are visiting is using SSL (HTTPS in the address bar), which means everything sent from your computer to the remote server is encrypted. Even if your company were to capture the data in-between, it would be encrypted. I say somewhat safe because if there is spying software installed on your computer, it can capture keystrokes and therefore capture whatever you type into those secure sites.
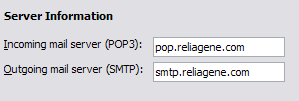
For your corporate email, you’re checking for the same thing, a local IP address for the POP and SMTP mail servers. To check in Outlook, go to Tools, Email Accounts, and click Change or Properties, and find the values for POP and SMTP server. Unfortunately, in corporate environments, the email server is probably local and therefore you are most definitely being monitored, even if it’s not through a proxy.
You should always be careful in writing emails or browsing web sites while at the office. Trying to break through the security also might get you in trouble if they find out you bypassed their systems! IT people don’t like that, I can tell you from experience! However, it you want to secure your web browsing and email activity, your best bet is to use VPN like Private Internet Access.
This requires installing software on the computer, which you may not be able to do in the first place. However if you can, you can be pretty sure no one is able to view what you’re doing in your browser as long as their is no local spying software installed! There is nothing that can hide your activities from locally installed spying software because it can record keystrokes, etc, so try your best to follow my instructions above and disable the monitoring program. If you have any questions or concerns, feel free to comment. Enjoy!
 We Provide service maintenance to almost all type of laptops -click on Here to find out more info. We offer you a no fix, no fee policy and will never charge more than a maximum of 5 hours for computer repairs to a single computer. Fast affordable computer repairs, laptop repairs and server repairs at your home ,business or our workshop.
We Provide service maintenance to almost all type of laptops -click on Here to find out more info. We offer you a no fix, no fee policy and will never charge more than a maximum of 5 hours for computer repairs to a single computer. Fast affordable computer repairs, laptop repairs and server repairs at your home ,business or our workshop. We Provide service maintenance to almost all type of desktop -click on Here to find out more info “We promise you to provide you a best quality service with the server capacity, performance and most importantly, the required reliability practically immediately.”
We Provide service maintenance to almost all type of desktop -click on Here to find out more info “We promise you to provide you a best quality service with the server capacity, performance and most importantly, the required reliability practically immediately.”
 We offers a range of services and consultation. With our in-depth knowledge and our excellent customer service skills we make sure you are treated right. . Just give us a ring and we will provide you 10 minutes free consultation. Come to our shop and we will help you save money as provide you technologies with warranties that can last long.
We offers a range of services and consultation. With our in-depth knowledge and our excellent customer service skills we make sure you are treated right. . Just give us a ring and we will provide you 10 minutes free consultation. Come to our shop and we will help you save money as provide you technologies with warranties that can last long. We build small, low cost websites for you. We focus on simple but look very professional, effective, high-quality websites, with fast delivery. You get Content Consultation, Hosting, 15 FREE Email Addresses, Search Engine Optimisation, Content Management System.
We build small, low cost websites for you. We focus on simple but look very professional, effective, high-quality websites, with fast delivery. You get Content Consultation, Hosting, 15 FREE Email Addresses, Search Engine Optimisation, Content Management System. Need Business Card, just give us a ring and we will prepare a random designs and make sure you can choose the best one before we print and deliver to your door with no extra cost! Importance of Business Carde. Many people forget that a Business Card is a silent salesperson – it carries on your job, long after you have gone home. Work it harder by adding a cut-out shape, or double your selling space with a folding business card.
Need Business Card, just give us a ring and we will prepare a random designs and make sure you can choose the best one before we print and deliver to your door with no extra cost! Importance of Business Carde. Many people forget that a Business Card is a silent salesperson – it carries on your job, long after you have gone home. Work it harder by adding a cut-out shape, or double your selling space with a folding business card. If you company has just started, 1-Year Hosting would be perfect for you. From hosting the smallest web site to the biggest web infrastructure projects, our team of experts help Kiwi developers deliver amazing web projects. Join us to experience local web hosting supported by the best team in the business. Click on HERE to see all Hosting Table Matrix
If you company has just started, 1-Year Hosting would be perfect for you. From hosting the smallest web site to the biggest web infrastructure projects, our team of experts help Kiwi developers deliver amazing web projects. Join us to experience local web hosting supported by the best team in the business. Click on HERE to see all Hosting Table Matrix
.jpg)
























